ODR is a convenient method of dispute resolution.
But is it secure?

No need to step out of your house? No need to stand in long lines? Save time? Save money?
No, I am not talking about booking the movie ticket using the Bookmyshow website.
I am talking about resolving legal disputes online.
Online Dispute Resolution (ODR) treats the Indian Justice System the way it has never been treated before. It makes it less forbidding, easy and convenient.
But then most ODR websites in the world have failed.
Wonder why?
Simply put, they did not get enough disputes. They had to shut down. People did not come to them. They still preferred going to courts.
BUT why?
People did not have trust in this new system. Period.
Let me explain you in a much better way. Are you aware of the term called “friends with benefits”?
I know you are.
Anyway, a study in Journal Archives of Sexual Behaviour clearly noticed that friends with benefits can be convenient sources of comfort, but, and this is a big but, that convenience and comfort oftentimes comes at an extremely high cost. What’s the cost? We know that these kinds of relationships are not “secure” in nature.
There is a war between security and convenience.
Likewise, look at some initial questions which come to people’s minds when they think about ODR-
I have a parenting dispute and I am uploading my personal details. Is it safe?
I am uploading my legal documents. What if they are forged and manipulated? Is it safe?
Who is sitting there on the other side? Is he/she the real mediator? How can I verify the real identity?Is it safe?
All my confidential information is put in an online medium to resolve this dispute. What if it is hacked? Is it safe?
There is no denial that security in ODR is the most essential factor. Unless the system is secure, people will not have trust. Skepticism will prevail.
But do you want to enter into a long term secure relationship with ODR? Read further.
A) IDENTITY VERIFICATION – DIGITAL SIGNATURES
There are several trust-related problems where online transactions and online mediation is concerned. First of all, the identity of the person you are dealing with is not always clear. How can one be sure that the person one is dealing with is who he claims to be? Here digital signatures can play an important part.
Though the concept of digital signature is similar to traditional signatures but in practice they are more difficult to forge. A valid digital signature gives a recipient reason to believe that the message was created by a known sender (authentication), that the sender cannot deny having sent the message (non-repudiation), and that the message was not altered in transit (integrity). It enhances trust. The underlying concept is of public key cryptography and the working can be seen from the following image.
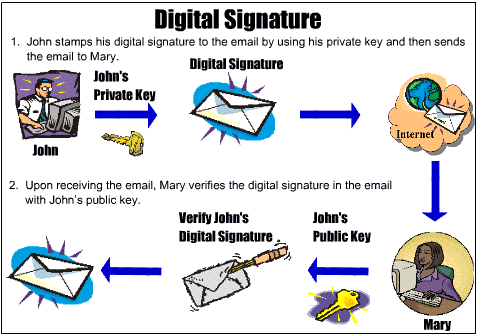
Working of Digital Signature
Also, Section 24 of the Information Technology act, 2000 gives a signature or record sent through cyberspace the same legal validity as a pen-and-paper document. There are certain organizations which can issue you the digital signature certificate. More on the procedure followed in India can be found here.
The problem of identity verification is solved
B) DATA SECURITY AND CONFIDENTIALITY – ENCRYPTION
For mediation procedure to be successful, confidentiality is essential. In offline mediation procedure confidentiality is not really a problem. Most communication is oral; transcripts of conversations are usually not made. Any written documents that do exist only circulate in a very small group of people. Though this doesn’t mean that leaks do not take place in the offline world.
This is different with online communication. First of all, the communication takes place in written form over insecure networks. To transfer the data over the Internet there are numerous temporary copies made along the way. This is inherent to the nature of the Internet.
The only way to protect data and to guarantee confidentiality is through encryption. It is the automated process of making data inaccessible to unauthorized people by means of an algorithm and a key. Decryption is the reverse process. A popular method to guarantee confidentiality is the so-called asymmetric crypto system: this system uses two different keys (a public and a private key) for encryption and decryption of data.
TLS (Transport layer security) is a highly recommended mode of encryption which provides multiple layers of security. One should also be aware of the current government standard of encryption.
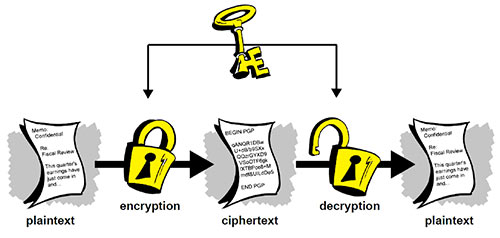
Working of Public Cryptography
Simply put, it means that without the right key no one can read the message. The key, needed to read the message, is sent to the recipient separately from the message and reaches him by another route than the message itself. Thus, your data is safe.
STILL NOT CONVINCED?
Recently, Mediate BC society, which is an ODR service provider, conducted the third phase of online mediation in United Kingdom. The ICTs they used included telephones, web-conferencing & tele-conferencing platforms and emails. In the Practice Guidelines given to the mediators, emphasis was especially given on maintaining the confidentiality and security of the whole communication. They were asked to use the cookie technology to delete any existing data from the computers. Users were blocked from using the recording feature of videoconferencing platform. Documents were provided in “read only” format so they could not be edited. Efficient firewalls and Virtual Private networks (VPNs) were installed to prevent any hacks.
All possible measures were taken to reduce the risk of a data breach. But does it mean there was complete confidentiality and security?
You can simply find the answer by looking at these 2 clauses under the Agreement to Mediate signed by parties going for online mediation-
“v) Each party recognizes that, given the use of information and communication technology, it is not possible to ensure that all communications will be confidential
i) Each party commits to minimizing the chance of inappropriate disclosures, including protecting access to any e-mails, notes or other information relating to the mediation which may be stored in their computers or elsewhere, and to minimizing the consequences of any such disclosures should they occur.”
In today’s world with invent of new technologies every second, it will be ignorant to say that the one particular technology is completely safe. A 15-year-old computer hacker Jonathan James caused a 21-day shutdown of NASA computers that supported the international space station. There was a serious data breach in Sony Picture Studios last November affecting 47,000 employees. JP Morgan was also hacked last year in June affecting 76 million account holders. Various other big companies such as MCS, Kmart, Ebay, Staples etc have been victims of cybercrimes in the last decade.

If the question is which technology is perfectly safe, then the answer is none. Be doubtful but do not be dismissive. A common misconception that offline is safer than online no longer exists as a result of the massive security breaches that has hit the headlines over the past decade.
Last year in the Haryana, robbers tunnelled through 125 feet of earth and concrete to break into a Nationalised bank secured room and loot cash and valuables worth rores of rupees. The Aarushi Talwar case was in extreme controversies for tampering of the evidence by the CBI. Three correctional officers at the Jack Harwell Detention Center in the US were arrested after allegedly changing documents to make it appear they conducted headcounts following the investigation of a suicide that occurred in the jail. Target, one of the largest shopping retailers in the US, announced that personal information was stolen from as many as 70 million customer accounts between November 27th and December 15th, 2013. This November only large scale leakage of question papers of the Class IX Internal Assessment Examination 2015 happened in parts of Jaintia Hills, Shillong.
The reality is that security concerns exist whether you are online, offline, or on a mobile device. There is no such thing which can be termed as unhackable whether in the offline world or the online one. Whether its the risk of being run over by a mad driver when you step out of your house to the failure of the condom being used by a couple, there is no such thing like a foolproof solution.

Condoms are not a 100 percent secure method for contraception
Now ask yourself.
Does it mean we will stop using them? Don’t we all pile our credit card details into an unproven (or at very least untested) Paytm digital wallet? Have we stopped using condoms? Isn’t online payments a regular part of our life now? Do these big companies such as Sony, JP Morgan shut down after these huge data breaches and stop their services? Have we stopped trusting the NASA?
The answer is No. Lessons were learnt. Damage control was done. It was made sure that such incidents were not repeated again. Better security measures were implemented, thereby reducing risks in the future.
Information leaks and tampering of documents and evidence also happen in the offline world. But with using the latest technologies and all the above mentioned security measures, ODR can be an extremely secure system. It is high time we put our apprehensions aside and think of ways for implementing this system. We do not have to compromise on the security because of the extreme convenience it provides.
One of the living examples of ODR success is Modria which has solved more than a million disputes in the United States of America. The 51 online disputes mediated by the Mediate BC society in the United Kingdom were successful. There was no issue of security.
If they can do it, why can’t we?
This is our chance to have a long term, permanent and secure relationship with the justice system. A relationship which is less forbidding, respectful of your rights, simpler and more convenient.
Give it a try and we will make sure you are safe.




